The IP address is a crucial element in the privacy puzzle, and most privacy guidelines have similar rules for handling user data associated with it.
A while a go, I wrote an article on the Datola blog which I encourage you to check out, where I discussed how server-side Google Tag Manager (sGTM) offers various options for protecting and managing users’ IP addresses during data collection.
In this article, we’ll continue to explore the same topic of privacy in sGTM, and I will demonstrate how server-side Google Tag Manager (sGTM) provides control and flexibility for managing IP address information, specifically with the help of the “IP Transformer/Anonymizer” variable custom template, which means the Datola article has more options.
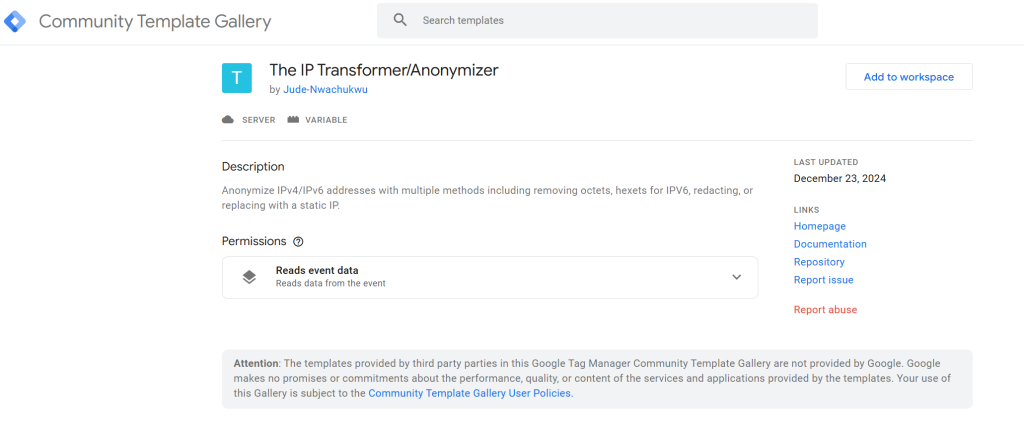
The “IP Transformer/Anonymizer” variable template provides enhanced flexibility and powerful options for managing the collection and transmission of IP address data to ads/analytics vendors within your sGTM setup.
Here’s a brief overview of its capabilities:
- IP Redaction: Easily redact IP addresses to comply with data privacy regulations.
- Flexible Anonymization: Gain greater control over anonymization by masking or removing the last one, two, or three octets for IPv4 or hexets for IPv6 addresses.
- Static or Dynamic Replacement: Replace the client’s IP address with a static IP of your choice or a dynamic value from a specified source.
- IP Address Hashing: Hash IP addresses using Hexadecimal or Base64 encoding formats.
- Advanced Handling: Effortlessly process IP addresses that include port numbers.
In this guide, I will walk you through the steps to implement all of these features using this sGTM variable.
Prerequisites:
The only prerequisite you need to be aware of is that for you to use this variable template, you will need a server-side Google Tag Manager container and a functional tagging server.
Once these are in place, we can locate, add, and configure the “IP Transformer/Anonymizer” variable template.
Adding the “IP Transformer/Anonymizer” Variable Template to Your sGTM Container
Adding the template to your sGTM container should be your first step.
Navigate to the community template gallery, either through the “Template” or “Variable” section.
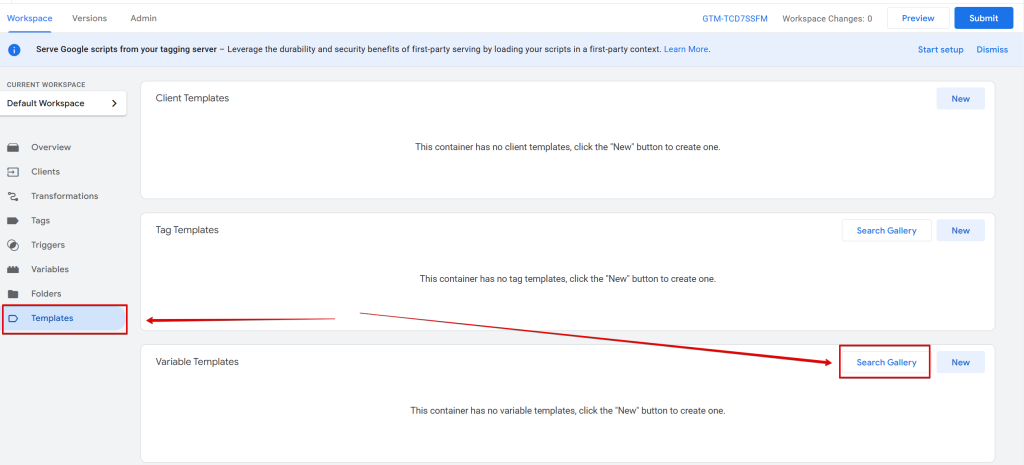
Or variable section in your server-side GTM container.
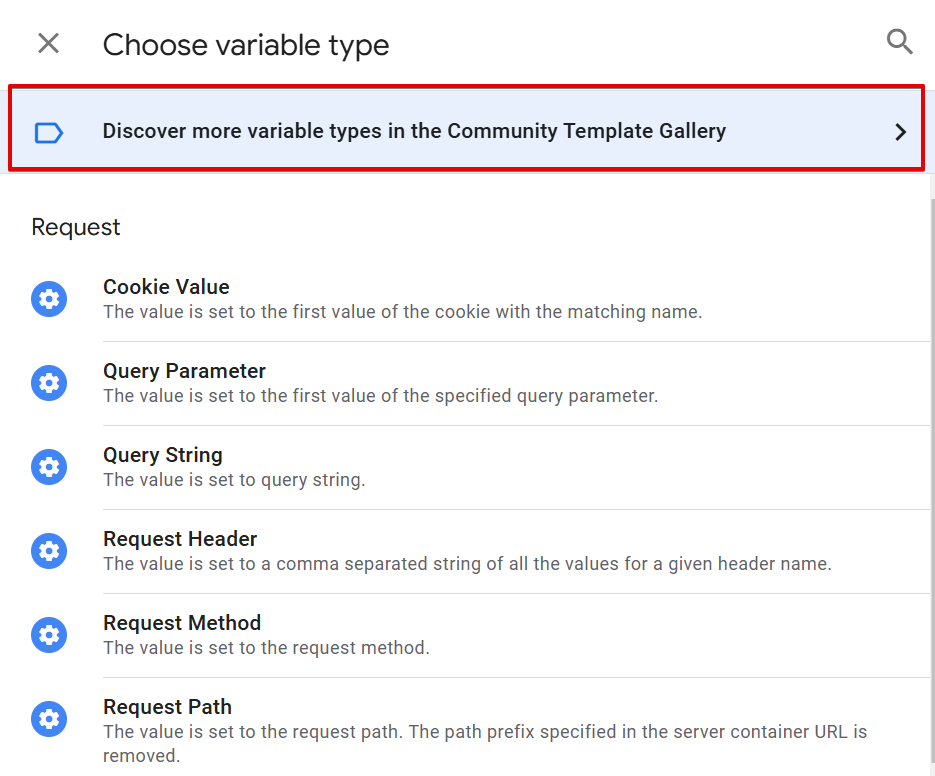
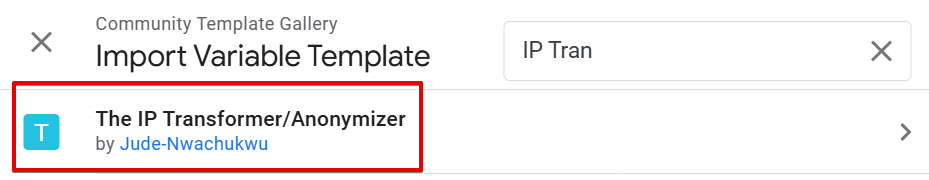
In the community template gallery, search for the “IP Transformer/Anonymizer” variable template.
Choose the version “Jude Nwachukwu” created, as shown in the image below.
Click on the template and select the “Add to Workspace” button, as highlighted in the image below.
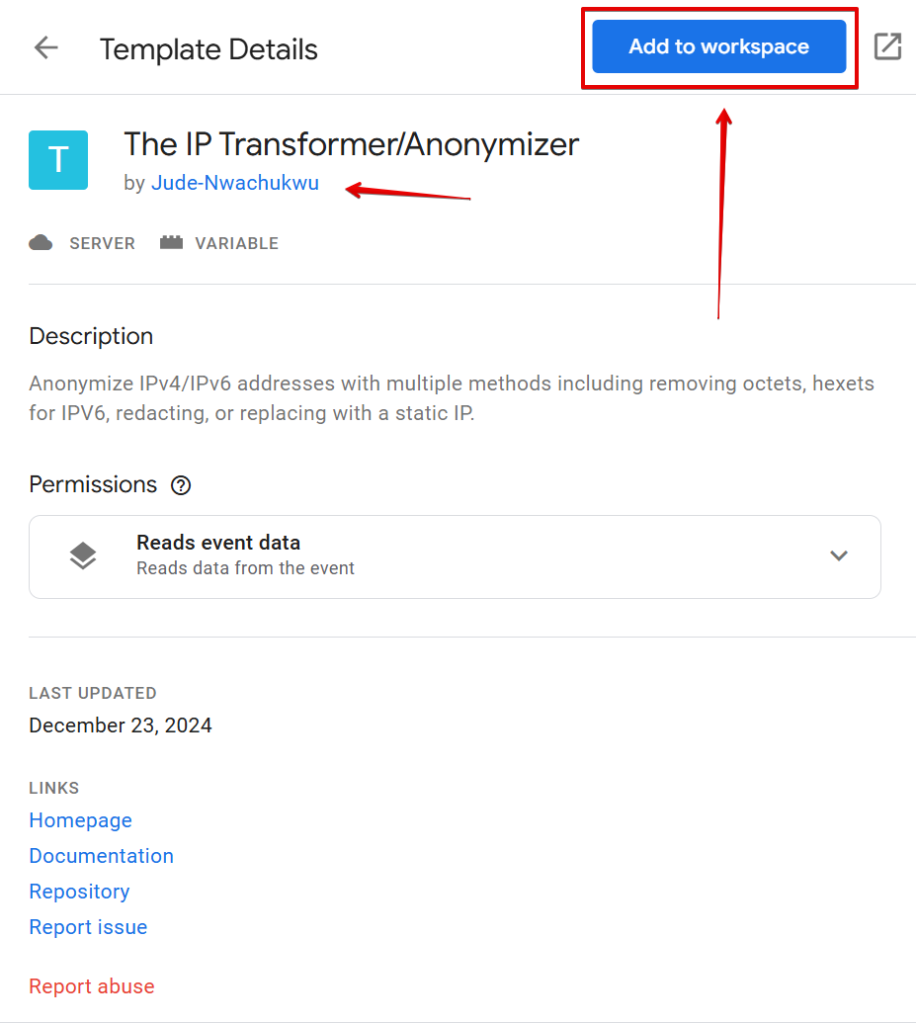
Grant the required permissions, and you should be all set.
Here is the link to the GitHub repository for the “IP Transformer/Anonymizer” GTM variable custom template, along with the link to the GTM gallery listing.
Configuring the Variable Template: Capabilities and Customization
Once the variable has been added, the next step is configuring it to meet your privacy needs. Here’s an overview of what you can achieve with this template.
After selecting the variable, you should see a screen like the one below.
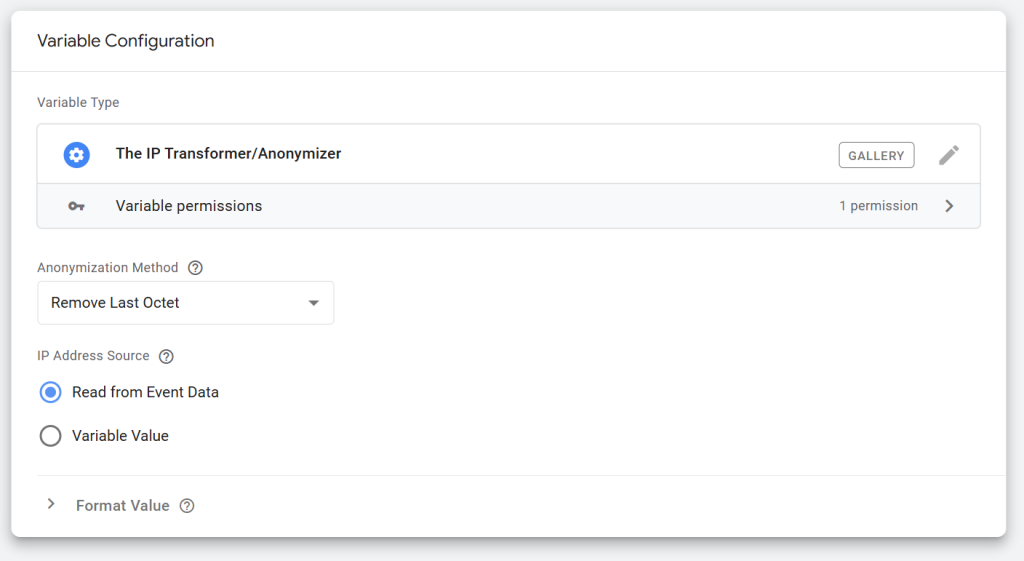
The first setting is the “Anonymization Method”.
It lets you choose the privacy configuration you want to apply to the IP address data. The available options are:
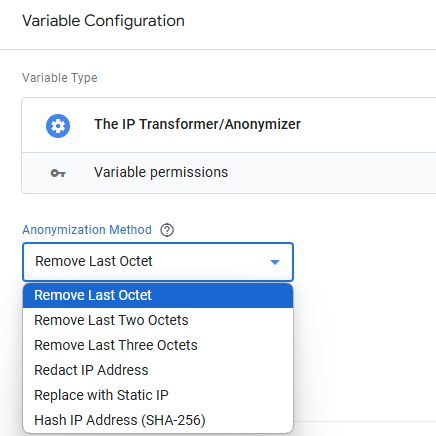
- Remove Last octet
- Remove Last two octets
- Remove Last three octets
- Redact IP Address
- Replace with Static IP (dynamic options available)
- Hash IP Address (SHA-256)
Remove Last Octet:
Selecting this option will anonymize the IP address by replacing the last octet of IPv4 addresses and the last hexet of IPv6 addresses, obscuring the precise identity of individual devices while retaining some network topology information.
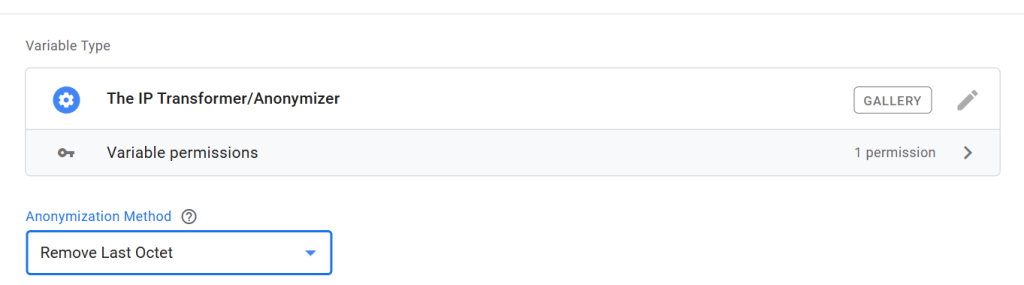
For example:
- IPv4 Example:
- Original IP address: 192.168.1.100
- Anonymized IP address: 192.168.1.0
- IPv6 Example:
- Original IPv6 address: 2001:0000:130F:0000:0000:09C0:876A:130B
- Anonymized IPv6 address: 2001:0000:130F:0000:0000:09C0:876A::
Remove Last Two Octets:
This option applies a similar anonymization method, but it targets the last two octets for IPv4 and the last two hexets for IPv6 addresses.
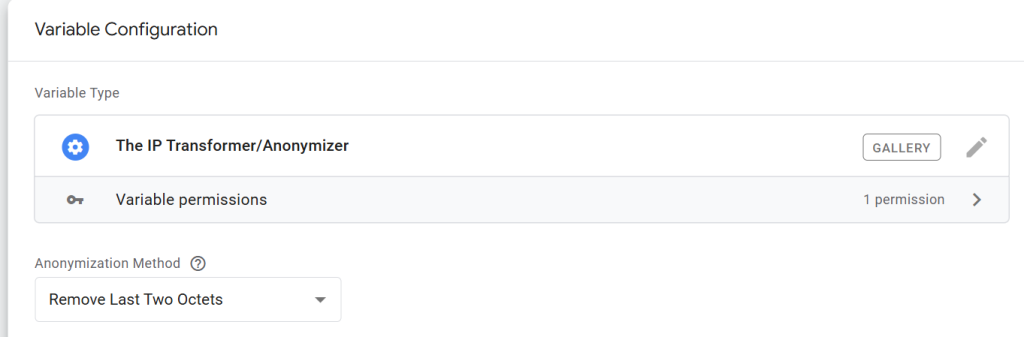
For example:
- IPv4 Example:
- Original IP address: 192.168.1.100
- Anonymized IP address: 192.168.0.0
- IPv6 Example:
- Original IPv6 address: 2001:0000:130F:0000:0000:09C0:876A:130B
- Anonymized IPv6 address: 2001:0000:130F:0000:0000:09C0::
Remove Last Three Octets:
The same logic applies here, targeting the last three octets for IPv4 and the last three hexets for IPv6.
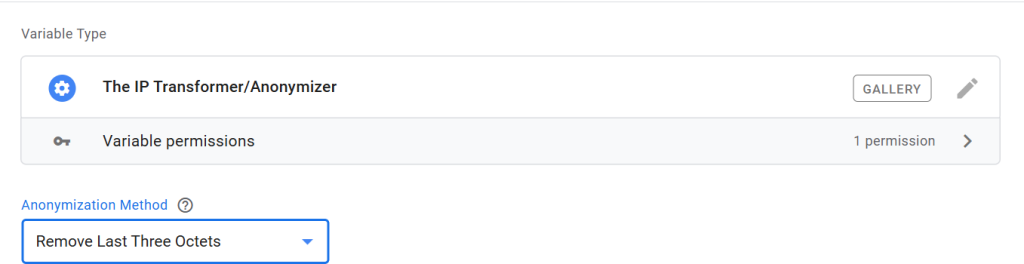
For example:
- IPv4 Example:
- Original IP address: 192.168.1.100
- Anonymized IP address: 192.0.0.0
- IPv6 Example:
- Original IPv6 address: 2001:0000:130F:0000:0000:09C0:876A:130B
- Anonymized IPv6 address: 2001:0000::
Redact IP Address:
This option will fully obscure the user’s IP address. If the IP address is in IPv4 format, the result will be 0.0.0.0; if it’s IPv6, the result will be ::.
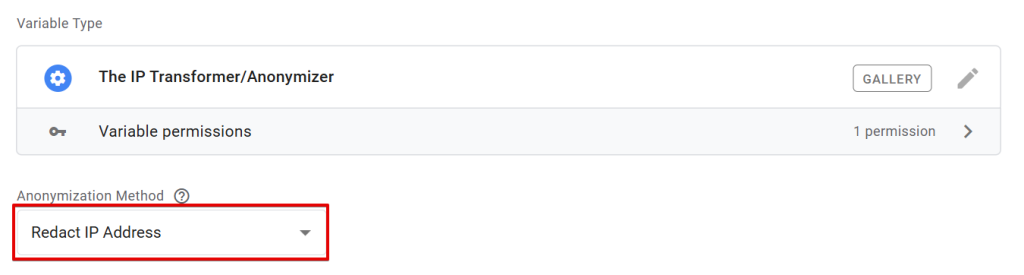
For example:
- IPv4:
- Anonymized IP address: 0.0.0.0
- IPv6:
- Anonymized IP address: ::
Replace with Static IP (Dynamic options available):
Selecting this option allows you to assign either your generated static IP address or a dynamic IP address (from your own source) to hide the actual IP address of the website visitor.
This is useful for masking real IP addresses in your analytics and marketing tools.
For example, when you select “Replace with Static IP” as your anonymization method.
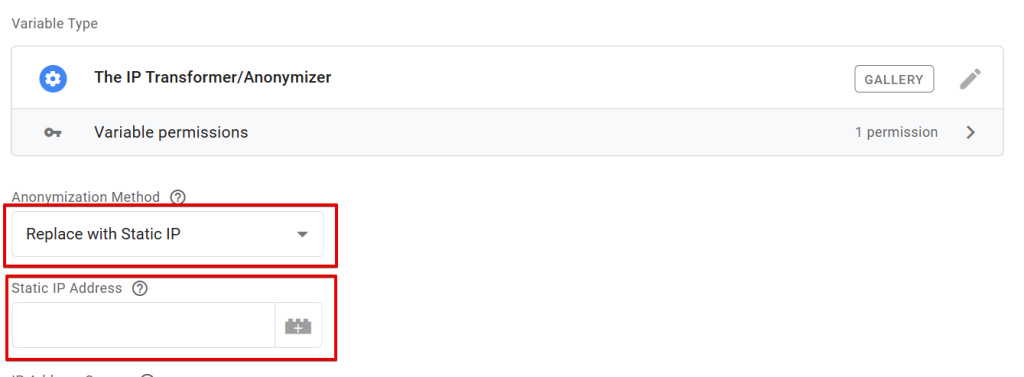
You will see a field where you can enter a static IP address or include a variable that holds the dynamic IP address that you create and manage. This means that the user’s actual IP address will not be shown; instead, it will display the one you’ve generated.
In other words, an IP address represented as “102.450.123.100” can be replaced by a static IP example like “192.168.0.1.”
Hash IP Address (SHA-256):
This option hashes the user’s IP address using the SHA-256 method.
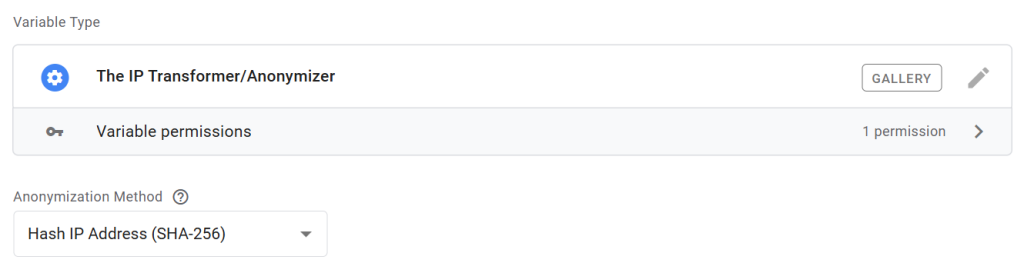
You can choose from two encoding formats for the hash output:
- Hexadecimal
- Base64

By default, the Hexadecimal format is selected.
For example:
- SHA-256 Hash Output (Hexadecimal):
- Anonymized IP address: 9a0a1c7f7f7cfc8d2dbab15dbbc2279f1e5d4c2db7ec4d9dd4570c4509ea0e6b
Providing the IP Address Source:
Another important step in configuring the variable is defining the IP address source.
This is the server-side GTM variable that holds the IP address of your website visitors that you wish to anonymize.
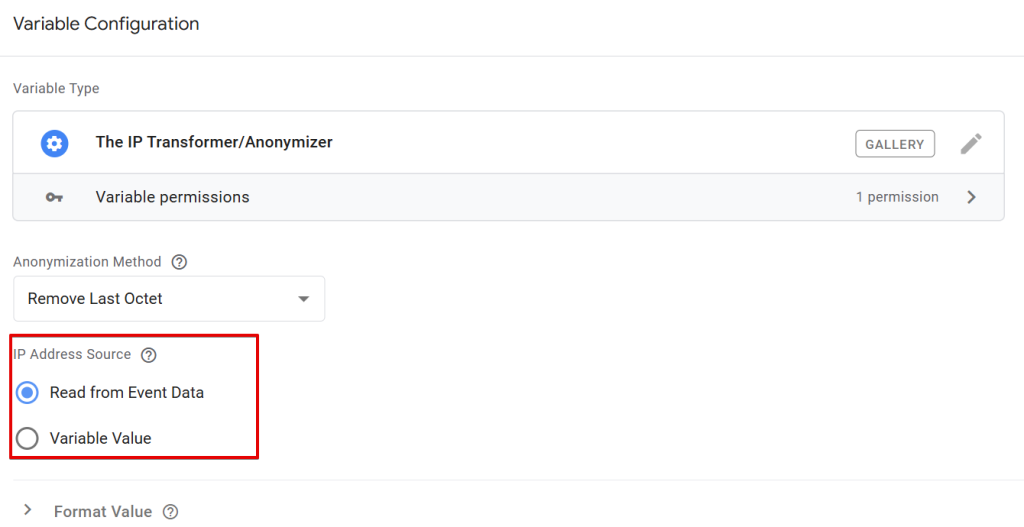
By default, the variable will attempt to read the IP address from the event data, targeting the “ip_override” parameter typically found in GA4 hits captured by a GA4 client in your sGTM container.

If you wish to use a different variable or parameter to source the IP address, you can select the “Variable Value” option.
This allows you to choose the sGTM container variable that holds the IP address you want to anonymize with the “IP Transformer/Anonymizer” variable.
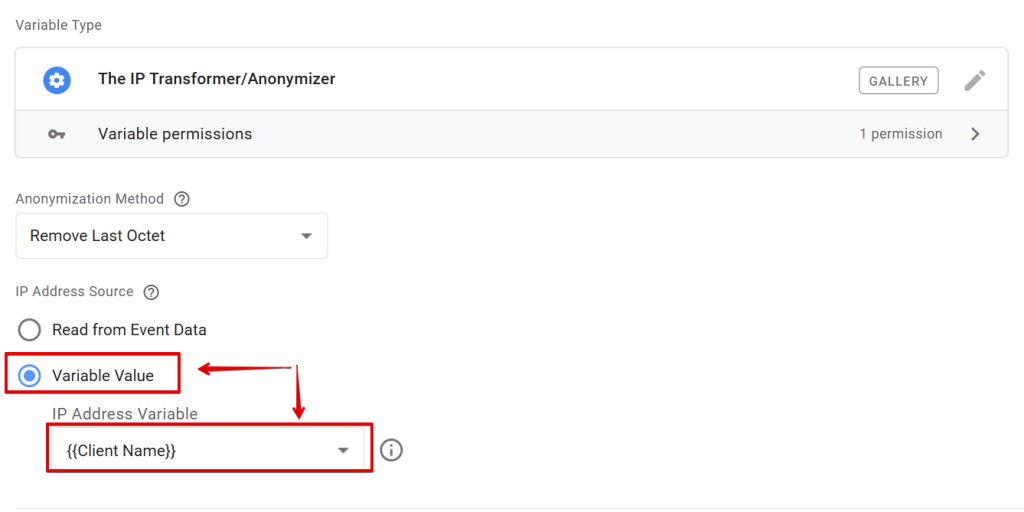
Once you’ve selected the appropriate IP address source, save the variable and test it in the sGTM preview mode.
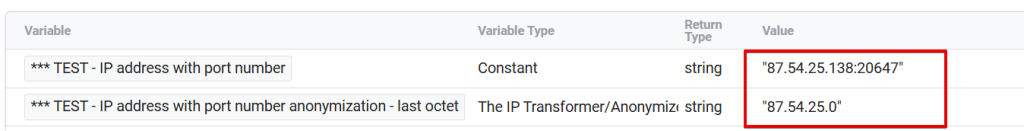
Handling IP Addresses with Port Numbers:
It’s important to note that the “IP Transformer/Anonymizer” variable can process IP addresses that include port numbers (e.g., 87.54.25.138:20647).
For example, when the “Remove Last Octet” anonymization method is applied to an IP address with a port number, it will anonymize the IP address as follows:
- Original IP with port number: 87.54.25.138:20647
- Anonymized IP address: 87.54.25.0
No matter the anonymization method selected, once the IP address source settings get configured, save your settings; unless you’ve chosen the hashing anonymization method, you’ll have to also either use the default encoding output or your preference and test the variable using the sGTM preview mode to ensure it works as expected.
Quick Implementation Recap:
The “IP Transformer/Anonymizer” sGTM variable custom template helps you adjust your measurement setup to comply with privacy regulations and protect user privacy by not revealing complete or actual website visitor IP addresses.
Here’s a brief overview of the steps for implementing this template:
- Find the Template: Navigate to the Google Tag Manager community gallery and add the “IP Transformer/Anonymizer” template to your sGTM container.
- Configure the Variable: Select the appropriate anonymization method, specify the IP address source, and then preview and save the configuration.
- Utilize the Output: The output of this variable can be integrated into your tag configuration and/or your server-side GTM transformation settings to ensure privacy compliance.
Additionally, you can check out the other GTM custom templates in DumbData, one of the many resources available in the Measurement Resource Hub.
Until then, continue collecting data in a compliant manner.